Reviving & Securing an Enterprise Switch (Cisco Catalyst 2960-X Password Recovery)
Project Overview
This project documents the recovery, reset, and reconfiguration of a previously locked Cisco Catalyst 2960-X enterprise switch. The switch had unknown login credentials and had not been used in a while. I recovered console access, bypassed the password protection, performed a full configuration wipe, and verified system integrity. This sets the foundation for integrating the switch into my home lab environment for future VLAN, trunking, and routing projects.

Stack Used
-
Cisco Catalyst 2960-X (24-port PoE)
-
Tera Term (terminal emulator)
-
Console cable (RJ45 to USB via USB-serial adapter)
-
Windows 11 (management workstation)
1. Initial State: Unknown Switch, No Access
The switch was given to me with no working login credentials. Powering it on resulted in a “Username:” prompt with no way to authenticate.
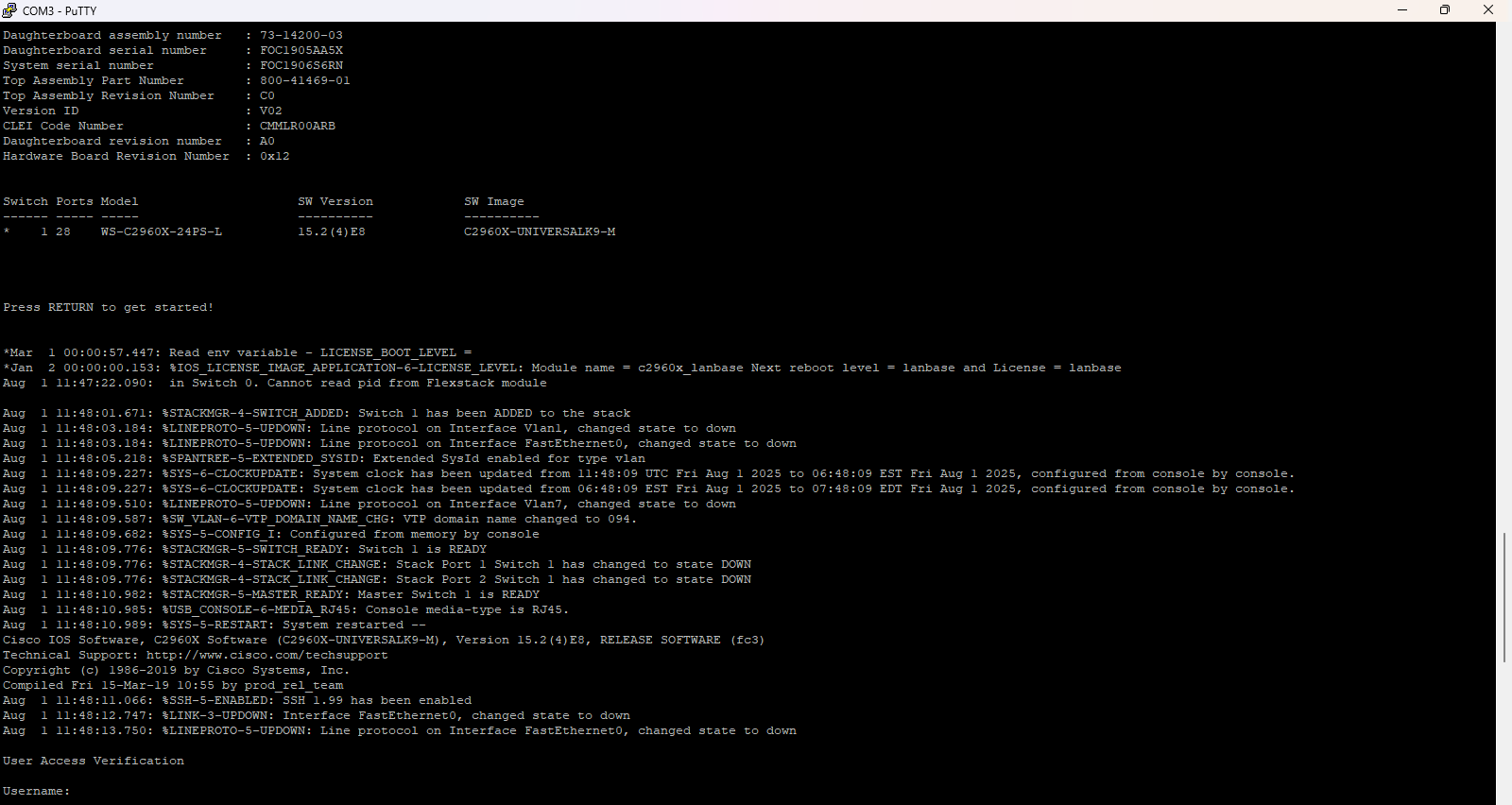
2. Connected via Console Cable
I used a USB-to-Serial adapter connected to a blue Cisco RJ45 console cable, then opened a session with Tera Term using the correct COM port (found via Device Manager).
Settings:
-
Baud rate: 9600
-
Data bits: 8
-
Parity: None
-
Stop bits: 1
-
Flow control: None
Side note: PuTTY failed to send Break during boot. Tera Term worked after I spammed Break from the “Control” menu and hit the MODE button on the switch simultaneously.
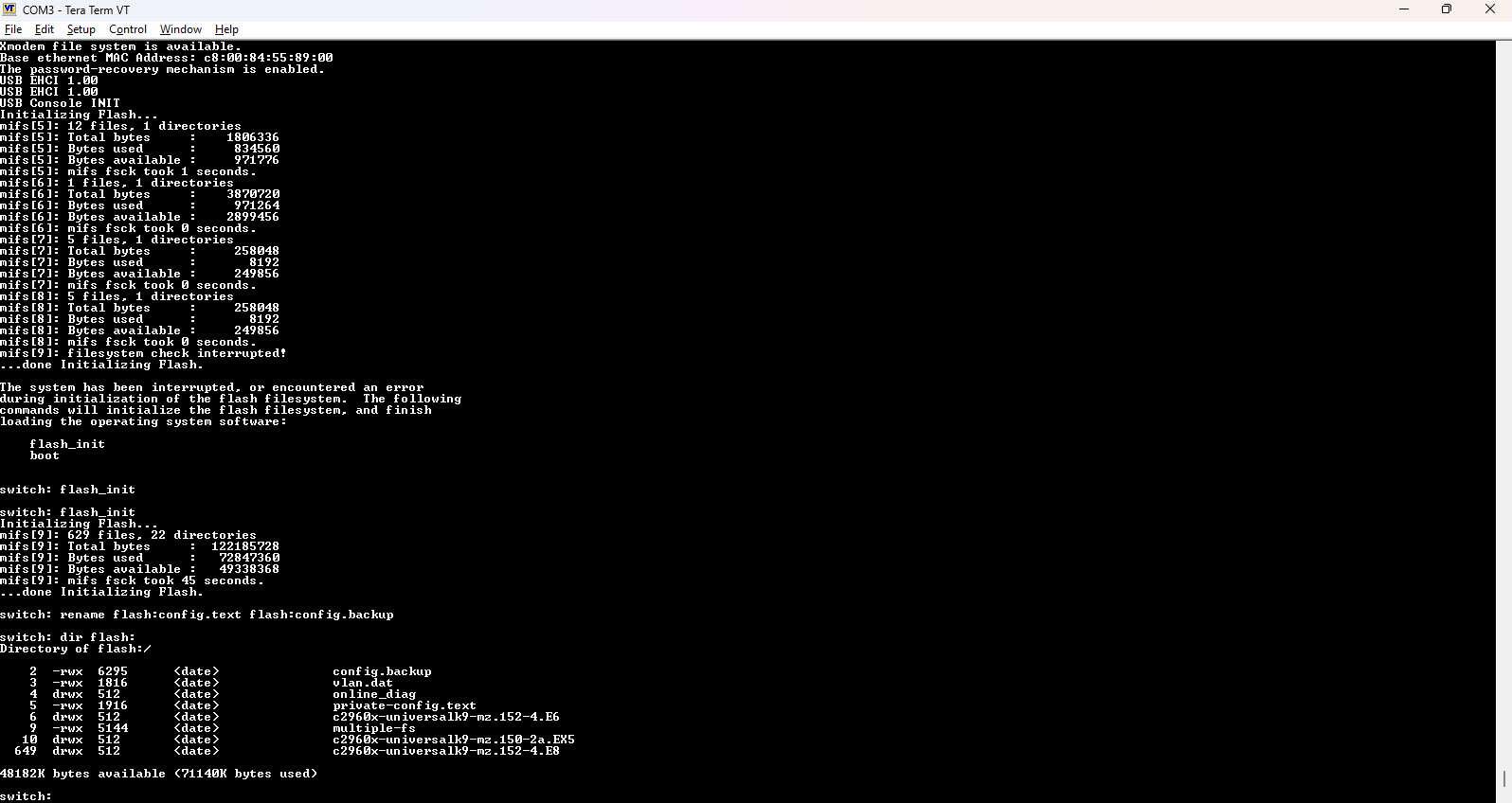
3. Entered Boot Loader Mode (switch: prompt)
Once in switch: prompt, I had access to the ROMMON bootloader. This allowed bypassing the startup configuration file.
flash_init
Breakdown
- Initializes the flash filesystem to allow file access (needed to rename the config file).
rename flash:config.text flash:config.backup
Breakdown
- Renames the startup config so the switch boots as if it had none. This avoids loading password-protected settings.
4. Booted Into IOS Without Config
boot
Breakdown
- Boots the normal IOS image from flash, now ignoring the renamed startup config.
--- System Configuration Dialog ---
Would you like to enter the initial configuration dialog? [yes/no]:
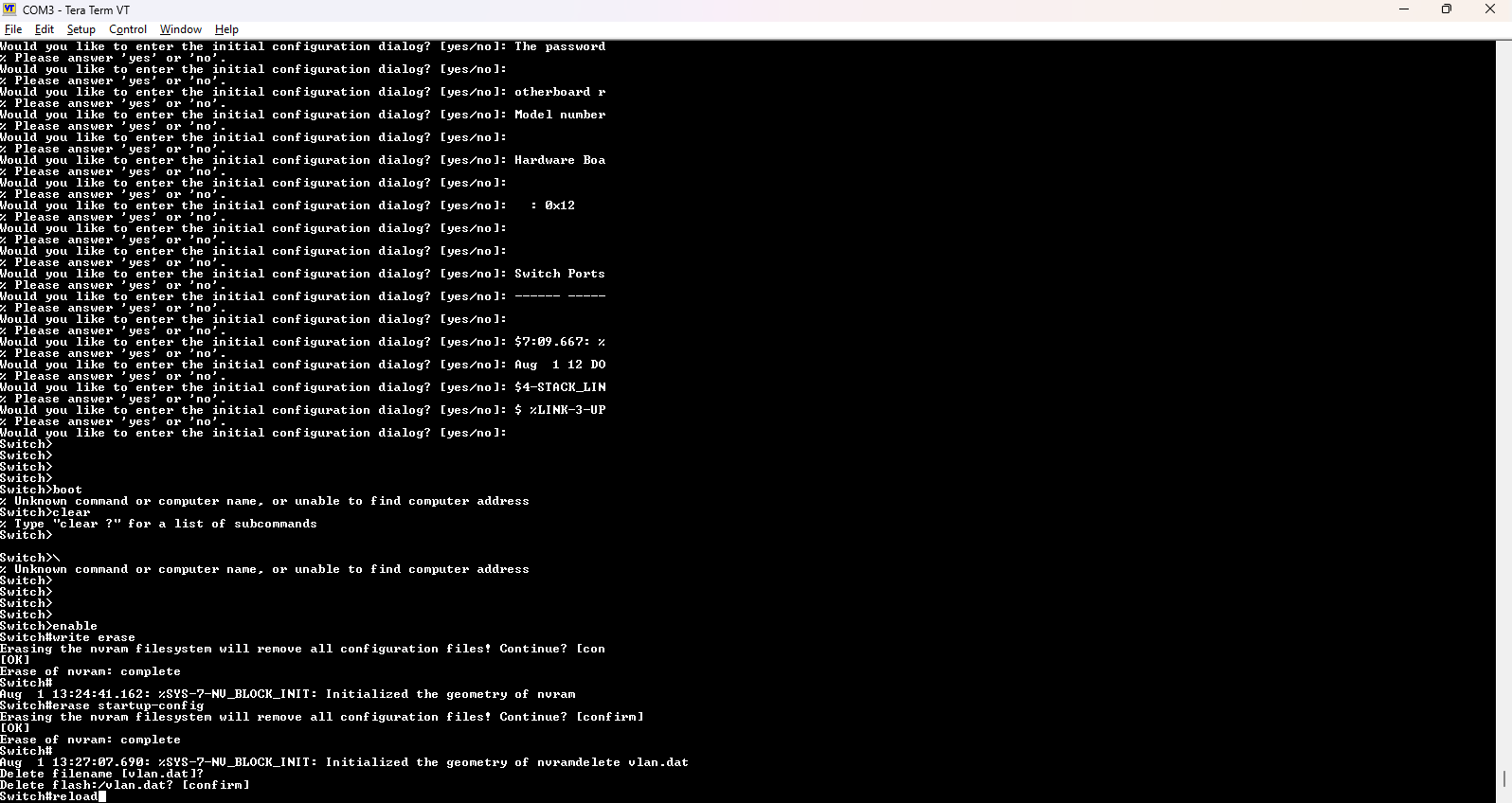
5. Erased All Residual Configurations
Once inside, I chose no and went into privileged EXEC mode.
enable
write erase
erase startup-config
delete vlan.dat
reload
Breakdown
-
write erase: Clears the running configuration -
erase startup-config: Double-wipes saved configuration -
delete vlan.dat: Removes all stored VLAN info -
reload: Restarts the switch to apply clean state
6. Verified Clean Boot
After rebooting, I was again presented with the configuration dialog, and verified:
-
No user accounts exist
-
No VLANs present
-
No SSH/crypto config
-
IOS image passed digital signature verification (proving authenticity)
Final Result
The switch is now fully reset and ready for secure integration into my home lab. I plan to use it for hands-on Layer 2 configuration, trunking, and simulating enterprise-level LAN setups.
What I Learned:
-
Console access isn’t enough; some cables block Break signals, Tera Term was key.
-
Password recovery mode works cleanly if flash is handled properly.
-
Cisco IOS will verify its own integrity if left unmodified, the switch self-validates.
-
Erasing config doesn’t touch the firmware, but that’s okay with verified signed images.
Next Up: Build a lab network with VLANs, DHCP snooping, and switchport security. This device will be the backbone of the lab.